LassPass Breach
Looking at the LastPass breach... Trust us when we say it is way worse than they want you to believe...
So why are we coming back to it again, what's new?
There are a few things that are going on here and we do want
to mention that it's not the users fault that this occurred.
LastPass needs to be accountable for what happened and the quick summary if you've enjoyed too much on the Festive Season
(heck we all did!) and don't know what's going on with LastPass….
Back in July/August of 2022, LastPass had a breach, and an attacker managed to construct a well-crafted phishing campaign and managed to gain access to a Dev
environment in LastPass, and steal the LastPass source code. Among other things, at
the time LastPass informed us all that no customer vaults were affected, that the attacker got access to some source code but it wasn't useful by itself, and that they had already taken measures to contain the breach and stop the access.
Well…. 😐
Just before Christmas on December 22nd, LastPass
sent out a press announcement with an update that they have had another breach
and in this breach, an attacker was able to use information gathered from the
August incident to create a more sophisticated and crafted phishing
campaign to gain access to LastPass employee credentials that then gave them
access to a backup environment where they were able to steal a backup of
literally a 100% of all the data that LastPass stores. It was literally
information gained in the first breach that was used to perform the second
breach. 🤯
This was no coincidence. They have always intended to gain that final source of information, so now we can sort of see a Kill-Chain process here. Picture the phases they went through
before they got what they wanted.
Many security researchers are out there picking out
LastPass for not just their handling of the incident, but rather how they are
misrepresenting what happened to try and push the blame off them.
We have been fortunate to be connected with several LastPass employees via LinkedIn for some time now. From our past communication with them, they appeared to be a rock-solid company. However, their handling of this incident has been quite alarming. It appears that they are trying to separate this into two incidents so that people don't realize they effectively mishandled the initial breach. They did not consider all the scenarios of what the attacker could do with the data they obtained. As a result, the attacker was able to do something they did not anticipate, and the breach got worse.
In the end, LastPass effectively suffered the worst breach possible for a password management company.
Now regarding the term they used, “Zero Knowledge Architecture” (LastPass themselves don't even know or are capable of viewing anyone’s password) - because they are fully encrypted and they do not store any master password anywhere on their systems.
Simply placed, as an example/scenario:
Supposing I had signed up to LastPass (before the breach), I
would naturally have a master password (which LastPass never sees), so this
would mean that my LastPass vault is encrypted “locally” and then uploaded to
them in an “encrypted” form.
Now that a breach occurred, when the threat actor got into
their data and stole a series of vaults, it would make sense that the vault is
already encrypted and due to Zero Knowledge, the Threat actor wouldn’t be able
to view the data inside the vault (my passwords).
If that were the case, I'd feel a lot better about what happened, because they don't have the master password, sure the threat junkie has my Vault, but what can they do?
Well…. 🥁
They could and obviously would start to brute force that password
using several tools that are already out there and as stated by LastPass themselves
during their press release - It would take millions of years to breach these
vaults 🙅
So, who cares if their vault was breached a million years
from now? 💀
Well... If that was actually the case, we definitely wouldn’t be
here writing this blog at this darn hour! 💤
The one major piece of info that had taken us by surprise was that we were always under the impression that LastPass encrypted your entire Vault locally and uploaded it, so LastPass just stored a fully encrypted Vault.
With this in mind, we were a little curious about how that worked since if you log into the web portal and into your Vault, they mentioned that it would download in your machine and memory (RAM) and decrypt in memory. So this means that it actually is always "Local". However, it turns out that they don't actually encrypt your entire Vault 🤯
It was confirmed that the password fields and the notes fields are encrypted, but none of the other fields were, and this is where they managed to piece together the other bit of information and crafted a well-structured and tailor-made (bespoke) phishing campaign for a set of employees.
LastPass choosing not to encrypt the entire vault really enables attackers to craft way better phishing emails than they did before and if you went to a phishing portal page where it pre-populated your username as well, you would trust it even more.
Now that we are where we are, let’s move on to remediation…
Whilst researching and reading several articles, we noticed lots
of people talking about “changing your master password” however, changing a
master password doesn't really matter to a certain degree because the attackers
stole a backup of your Vault and that backup has whatever master password you
had on it when it was stolen. If you change your master password (please do now) note that they still have a backup of your vault.
Remember they stole LastPass source code, so if they want to get creative, they can just fire
up their own environment easily and with the vaults they have in their
procession that are dated back from August 2022, they can setup up highly
sophisticated Brute force attacks against these vaults, which are separated from
LastPass infrastructure.
Let's call this new environment HackPass 😝 (Compiled and constructed by these Threat actors, within their own environment)
It definitely would be a good idea to change your master password right now, since you will be protecting yourself on your current Vault from the next hack.
The master password is what the attacker is going to really want to Brute Force because if they can get the master password they can unlock the rest of the Vault and if you are a LastPass admin for a corporate account and they can get into your account, then now they can unlock everybody else that you manage. That is definitely going to be a Target. 🞜
So with that in mind, let's discuss encryption.
LastPass mentioned that they used a type of protection on the master password which is called “pbkdf2”.
What is pbkdf2? We have no idea, never have we ever heard of
it before this event but after some research on google, we found some info
saying that “Password-Based Key Derivation Function 2 (PBKDF2) makes it
harder for someone to guess your account password through a brute-force attack.”
Source: https://support.1password.com/pbkdf2/
So what they actually trying to say is that this method is meant
to make it difficult to Brute Force through a dictionary attack, standard brute
force, or even rainbow tables, etc.
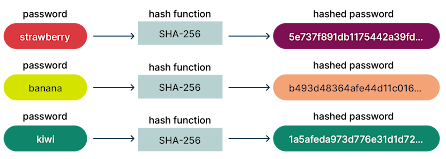
It's important to note that when we talk about passwords being "encrypted," it's not in the traditional sense of encryption, such as SSL. Instead, passwords are typically hashed, which means that they are transformed into a seemingly random string of characters. This hash value is then stored in a database, and when a user attempts to log in, the entered password is hashed and compared to the stored hash value. If they match, the user is granted access.
Scenario 2.0:
You have a password (let’s keep it simple) such as Banana.
If you run it through a hashing algorithm you would get a random string. Now if
I had to feed in Banana, Strawberry, Kiwi, etc, and look at the hash values that
come out of the same hashing algorithm and then compare the two and see if they
are the same. If they are, then I know I got the right password.
Now, with “Pbkdf2” which is the Password-Based Key Derivation
Function, this is an interesting way that does indeed make it stronger. So basically,
what you do is take a password and a random string of text and characters,
place those together and run that through your hashing algorithm which in this
case might be HMAC-256. Once that's done you get a string of text and then they
run that string of text through the hashing algorithm again (these are the iterations)
- iterations make it stronger because now you are basically having to reverse
all this hashing that's been done so this makes it really strong. Although, the iterations that they use are what
makes this not that great. The Pbkdf V2 is actually fine if you use it
correctly.
If you don't then it's weak.
LastPass was also quick to
announce that the default setting of iterations is “100100” that means every
time you encrypt a password in your LastPass Vault, your master password is run
through this hashing algorithm over a hundred thousand times. That may sound really impressive BUT, there are many internet standards out there (OWASP is
probably the biggest one) that recommend you do it over 300 000 times, so it's quite significant.
Earlier on, we mentioned how LastPass required a Minimum 12-character password or longer, now after some reading, we discovered that after implementing/enforcing this, they actually did not go back and correct those who had shorter passwords, and on the iterations, they did the EXACT same thing - when they launched as a company, they had it set to “1 iteration” (yes just ONE) and that is considered a serious crime today.
What is also quite alarming is that only after a few years later did they increase it and it wasn't that great either. They actually went up to 500, then 5 000, and eventually they went all the way to over 100k.
Now, considering this info, when everyone first heard of the
breach, IT Pros were logging into their corporate accounts and inspecting every sub-account they
had to confirm that it was indeed 100100 or higher, HOWEVER when some had
checked their personal accounts, they had seen figures in the 5-6k mark. So
definitely something you would want to check and confirm.
Moving on now....
What should you do?
Since we have already touched on the Master Password stuff, we weren't surprised that you need to immediately change every password that you have stored in LastPass.
Why?
Well if you are in Cybersecurity, you would already know of the Assume Breach principle, so treat it as such! Although Lastpass has some built-in features that would allow you to reset your passwords through their platform, we would seriously not recommend it as now we most certainly have lost trust in them.
If you are making use of the LastPass authenticator, then we would also strongly recommend that you move that off to another provider such as the Microsoft authenticator, etc. Note that Lastpass is not really sharing information as to when exactly the breach occurred and details on their other platforms as well (such as their Authenticator App as an example). With this in mind, we just have to assume that they were, and this means (if you are using their authenticator app) you would need to regenerate your OTP Keys.
Lastly, we actually would recommend that you move away from LastPass. Almost everyone online would recommend Bitwarden and/or 1Password. Migrating your data from Lastpass to these providers is simple, quick, and pain-free as well:
https://bitwarden.com/help/import-from-lastpass/
https://support.1password.com/import-lastpass/
To summarize and end off:
The LastPass breach that occurred in July/August of 2022 was actually worse than initially reported, including the second breach that occurred in December of the same year. The handling of the incident by LastPass has been criticized, with many security researchers pointing out that the company is misrepresenting what happened to shift the blame away from themselves.
Despite LastPass's claim that their "Zero Knowledge Architecture" makes it impossible for anyone to view customers' passwords, an attacker can brute force the master password and gain access to the encrypted vaults. While LastPass may not have been able to prevent the initial breach, their handling of the incident and failure to anticipate all possible scenarios has led to the worst possible outcome for a password management company.
Comments
Post a Comment